Jun 10
2020
Fraud Detection with Machine Learning For e-Commerce and Retailers

There is interesting research in Forbes’ recent article named “How E-Commerce’s Explosive Growth Is Attracting Fraud”. According to the statistics, e-commerce retail sales achieve 209% year-over-year revenue growth. It is expected that this indicator will grow, which means it will seduce fraudsters even more. This is a completely obvious pattern – big money always means a lot of attraction for attackers.
Is there a way to protect your business from these risks? We are sure there are. In this article, we will tell you how eCommerce fraud prevention and detection system work being powered by machine learning and artificial intelligence.
What Is Fraud in e-Commerce?
E-commerce and retail fraud mean any activity aimed at deceiving sellers or buyers in order to seize goods or money. In the e-commerce industry, all fraudulent transactions occur online. As for retail, fraud at the physical point of sale of goods is also possible. AI and ML solutions to encode expertise for detecting fraud in eCommerce and retail can handle both tasks.
What Are the Three Types of Fraud?
In fact, it is possible to identify more types of fraud depending on the nature of the crime, the level of damage, tools for committing fraud, and even unrealized criminal plans. Basically, it is possible to distinguish three main types of fraud.
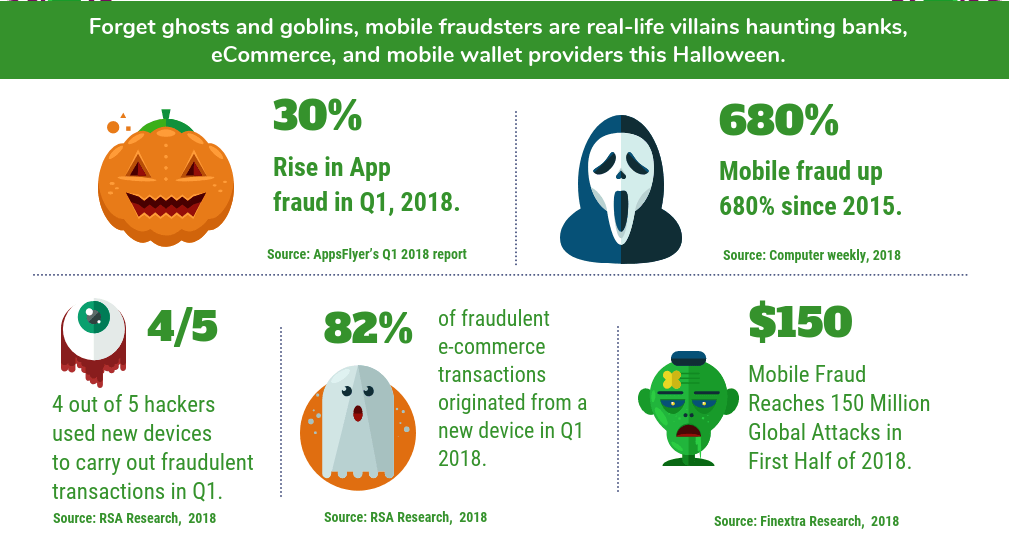
Mobile Fraud
This is a fairly logical phenomenon – the more users began to use mobile phones for instant transactions, the more scammers thought that these devices might have hidden potential. The infographic below illustrates the current situation with mobile fraud.
Moreover, this is the case when businesses and individuals are equally at risk. Very often, mobile fraud becomes a way of illegally making purchases on behalf of another person.
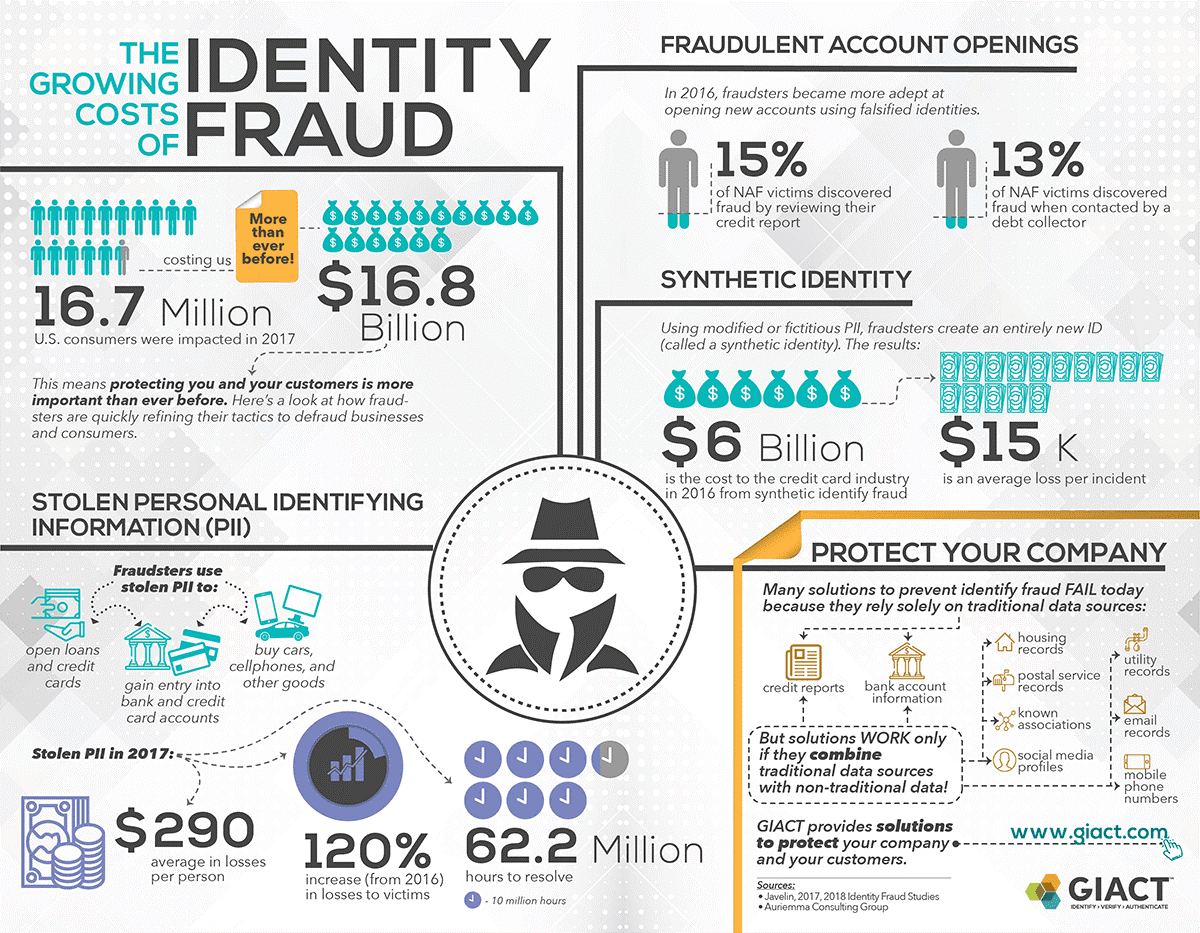
Identity Theft
Identity Theft is the second type of fraud that is very popular. Who do you think are the most frequent victims of this type of fraud? These are Millennials, the most active users of social networks and the most solvent category of the population at the same time.
The thing is that social networks allow you to make a portrait of a person and collect all the necessary data very easily. It’s not even necessary to hack anything. And comprehensive personal data also easily provides access to e-mail, and other applications, including financial ones.