
There is a huge debate on the topic is the internet, a great source of development and education for young people or is a boon that is responsible for killing all the privacy and security which are one of the most important parts of a service network. There were times when people used to log in to their accounts on other people’s phones and then without even logging them out they used to leave it just like anything.
The concept of cybercafes is one of the most dangerous parts as the person who is using a particular computer in the cyber Cafe is exposed to a lot of privacy and security threats in general known as cyber-attacks. Cyber attacks can be done in many forms and it is not just spam that you receive in your mail ID. As we know that cyber-attacks are at their peak nowadays, and there must be a lot of solutions in the market to prevent cyber-attacks to happen.
Penetration testing is one of the latest technologies for the prevention of cyber attacks.
- Black Box Approach:
The main thing about the software which is to be tested and to prevent cyber attacks is that the information about the software must be there for the better prevention of cyber attacks but at the same time in Blackbox approach, the same does not happen. The internal knowledge of the products must be known at the same time while the cyber attack is spoofed. But when we talk about the black box approach, then the same thing is seen to be invalid as the internal knowledge is not present in the product. The behavior of the software and also the attributes of the software at the same time are important but in the Blackbox approach, they both are not known.
- White Box Approach:
As discussed before the main thing about the software which is to be tested and to prevent cyber attacks is the information about the software which was not present in the black box approach. But when we talk about the white box approach then it is present and it is a major advantage for this type of approach. When we talk about testing practices, then we must make sure that it is done in the right way and under the system supervision of the developer as he is the source of the software. In the white box approach, the testing practices are done from the perspective of a developer. It is also known as structural testing.
- Grey Box Testing:
Grey box testing as the name suggest must be a combination of white and black which in itself when mixed produces grey color. When the white and black colors are mixed, then a grey color is formed and this type of testing method also indicates the same. All the positives of the black box approach or mix with the best positives of the white box approach to give a result as a grey box testing method.
By Pavel Novik, QA head of department, a1qa.
 Mobile health apps have raised the healthcare industry to a new level. Now consumers have an opportunity to track their blood pressure, pulse rate, input their symptoms that will then be analyzed by the ML app on the go. Without visiting the doctor’s office, we can now monitor our health condition and even connect with the provider by sending an in-app message and getting the consultation within hours.
Mobile health apps have raised the healthcare industry to a new level. Now consumers have an opportunity to track their blood pressure, pulse rate, input their symptoms that will then be analyzed by the ML app on the go. Without visiting the doctor’s office, we can now monitor our health condition and even connect with the provider by sending an in-app message and getting the consultation within hours.
No doubt, mobile health apps are now being developed at a high pace, however, not without dangers. Probably the most common cause of worry is how the software products approach security and data privacy issues.
With no opportunities to seal users’ health records, can we be sure that the confidential information isn’t exposed?
7 tips to help deliver a secure mHealth app
- Collect only the needed data
The main tip is: don’t collect the data you don’t need. Collect the information with the clear purpose and regularly dispose of the data you no longer need.
- Check the legal regulations (GDPR, HIPAA, COPPA, etc.)
Check the legal regulations your app is subject to. It is important that the app is developed in compliance with security and privacy requirements defined by the GDPR that outlines the procedures of handling EU citizens data, HIPAA and COPPA (a new child-oriented edition of which will come into force in 2020) in the US. According to all this, users, for example, have a right to ask you to delete any data you’re storing or explain the reason what you need this or that piece of data for.
- Include a section with Privacy Policy practices
Make sure your app has a section including Privacy Policy practices that comply with Human Interface Guidelines (for Apple) and Developer Guides (for Android) standards. Also, if you’re storing users’ data, you should get their consent to do so. Also, users should be able to revoke the consent at any moment.
- Make sure users’ data is not shared with any third parties
Ascertain that you don’t share the data of your users with any third parties, e.g. social media companies or advertising agencies. Enhancing user experience and monetization are the natural goals of any app developer but be careful with this. Recently a number of mHealth apps have been accused of sharing user records with Facebook. You don’t want to be among them, right?
- Send push notification without confidential data
If you send push notifications, ensure they don’t include confidential health data.
- Protect the app code
Different vulnerabilities may exist in the source code and may be caused by the developers’ error or lack of code testing. What can be done about this? Protect the code with encryption and run constant code scanning.
- Run security and penetration testing
Proper mobile app security and pentesting will include the following stages.
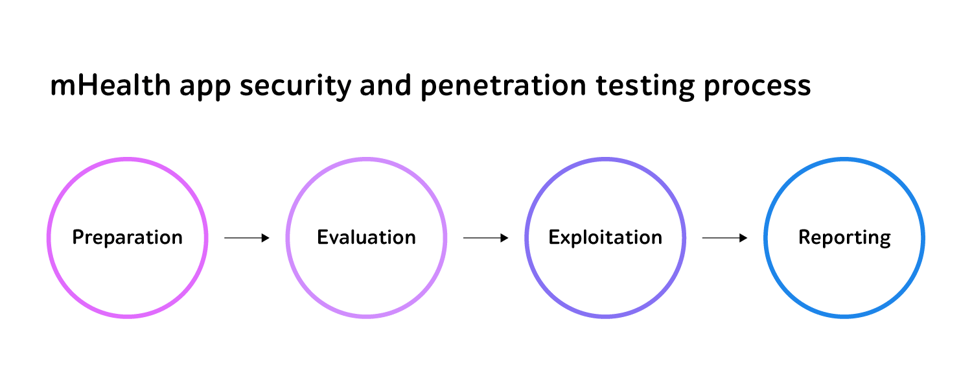
- Preparation – the testing team gets information about the software product and possible events that may lead to its successful exploitation as well as prepares test documentation.
- Evaluation – the QA specialists evaluate the current security level of the app and recognize the potential vulnerabilities.
- Exploitation – security test engineers act as hackers trying to make use of the discovered bottlenecks.
- Reporting – the team presents the results to the stakeholders and gives recommendations on how the security level may be improved.
Don’t forget about performance and UX!
Continue Reading

 Mobile health apps have raised the healthcare industry to a new level. Now consumers have an opportunity to track their blood pressure, pulse rate, input their symptoms that will then be analyzed by the ML app on the go. Without visiting the doctor’s office, we can now monitor our health condition and even connect with the provider by sending an in-app message and getting the consultation within hours.
Mobile health apps have raised the healthcare industry to a new level. Now consumers have an opportunity to track their blood pressure, pulse rate, input their symptoms that will then be analyzed by the ML app on the go. Without visiting the doctor’s office, we can now monitor our health condition and even connect with the provider by sending an in-app message and getting the consultation within hours.